Ethical hacking occurs when someone enters a computer or network to look for possible threats. Red teaming, penetration testing, and penetration testing are other names for ethical hacking.
Hacking is getting into a computer system by finding its weak spots to commit scams, steal data, invade privacy, or do other nasty things.
Ethical Hackers:
A hacker is someone who does theft by breaking into computers.
Hackers come in six different types:
- The Ethical Hacker (White Hat)
- Sticky Cracker
- Hat in grey
- Kids with scripts
- A hacktivist
- A Phreaker
Ethical hackers work in security and use their hacking skills to protect themselves. Ethical hackers use their skills to find security holes, write them down, and suggest ways to fix them to improve security.
Companies that offer online services or are linked to the internet need to have ethical hackers do security tests. Hacking in a good way is also known as penetration testing. The task can be done by hand or with the help of an automatic tool.
Ethical hackers are professionals who work in computer security. They try to get into a computer system, network, or app and break its protection. They find the weak spots and then make suggestions or give tips on strengthening the security.
Hackers use languages like Python, PHP, SQL, Ruby, Bash, Perl, C, C++, Java, VBScript, Visual Basic, C Sharp, HTML, and JavaScript.
Here are a few hacking certifications:
- CEH
- GIAC
- OSCP
- CREST
Following Are The Top 10 Hacking Tools Used By Ethical Hackers
#1) Nmap
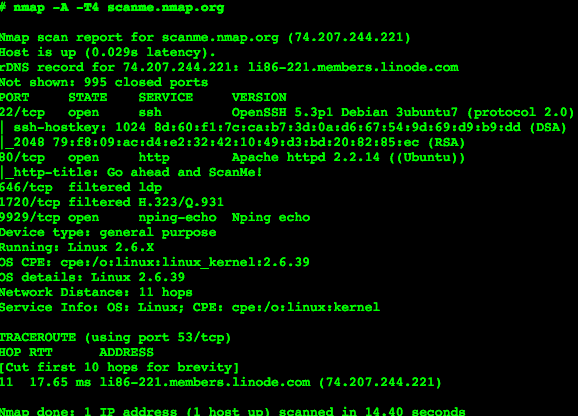
Price: free.
Nmap can check for security holes, open ports, and look around in networks. You can get it for free because it is open-source software.
Cross-platform works with it. This tool is versatile, allowing you to monitor the availability of hosts and services, create network inventories, and schedule service upgrades. It is compatible with individual hosts as well as large-scale networks, providing binary utilities for Linux, Windows, and Mac OS X.
Features:
The Nmap set has:
- Ncat is a tool for data movement, redirection, and debugging.
- Scan the results to compare usefulness (Ndiff),
- a tool for making packets and analyzing responses (Nping),
- Viewer for GUI and Results (Nping)
- By using raw IP messages, it can find out:
- Hosts that are available on the network.
- These people are willing to offer their services.
- Their operating system.
- What packet filters do they use?
- Along with many other traits.
- The best way to scan networks. It works quickly and is easy to use.
Website: Nmap
#2) Intruder

Intruder is a fully automated tool that looks for security holes in your digital assets, tells you about the risks, and helps you fix them. This is a great tool to add to your collection of ethical hacking tools.
Companies of all kinds can use Intruder to do enterprise-level vulnerability scanning because it has more than 9,000 security checks to choose from. Its security checks look for wrong configurations, missing patches, and typical problems with web apps like SQL injection and cross-site scripting.
Intruder, made by experienced security experts, takes care of a lot of the work of managing vulnerabilities so you can focus on what’s important. It saves you time by making results more relevant and scanning your systems for new weaknesses before they happen, so you don’t have to worry about it.
Along with Slack and Jira, Intruder also works with big cloud providers.
Website: Intruder
#3) Metasploit

You can get Metasploit Framework for free because it is an open-source tool. The paid version of Metasploit Pro is available. You can try it for free for 14 days. Get in touch with the business to find out more about its prices.
It is the programme used for testing for security holes. Using the Metasploit Framework, you can write and exploit code against an external machine. Cross-platform works with it.
Features:
- It’s helpful to know about holes in protection.
- It helps with security testing.
- Helps with the creation of IDS signatures.
- You can make tools for checking security.
- It is best for making tools that hide evidence and get around police.
Website: Metasploit
#4) Aircrack-Ng

Price: Free
Aircrack-ng has several tools for checking the security of a WiFi network.
All of them are command-line tools. It focuses on watching, fighting, testing, and cracking regarding WiFi security. Free BSD, NetBSD, OpenBSD, Solaris, and eComStation 2 are some operating systems it works with.
Features:
- You can use Aircrack-ng to target Replay attacks, de-authentication, fake access points, etc.
- It lets you save the info as text files.
- It can check the WiFi cards and drivers to see what they can do.
- The FMS, PTW, and dictionary attacks are all used to break WEP keys.
- Dictionary attacks are used to break WPA2-PSK.
- The best way to support any wireless network interface driver.
Website: Aircrack-Ng
#5) Wireshark

Price: Free
Wireshark is a packet analyzer that can look closely at many different protocols.
Cross-platform works with it. It lets you save the results in XML, PostScript, CSV, and Plaintext files. This feature lets you use colouring rules on packet lists, which makes analysis more accessible and faster. The above picture will show how the files are captured.
Features:
- The gzip files can be opened right away.
- To name a few, it can decode IPsec, ISAKMP, SSL/TLS, and more.
- It can record in real time and analyze data later on.
- It lets you look through the network data recorded using the GUI or TTY mode of the TShark utility.
- The best way to look at data bits.
Website: Wireshark
#6) OpenVAS

Open Vulnerability Assessment Scanner is a full-featured tool that can test without or without authentication and improve speed for large-scale scans.
It has a robust internal computer language and the features of many high-level and low-level internet and industrial protocols. The scanner runs tests to find holes in security based on a long past and daily updates.
Website: OpenVAS
#7) SQLMap

To find and use SQL injection flaws automatically, SQLMap is a tool that lets you take control of database systems.
It’s an open-source tool with a robust system for finding things. It works with MySQL, Oracle, PostgreSQL, and many other databases. It fully supports six types of SQL injection: error-based, time-based blind, Boolean-based blind, UNION query-based, stacked queries, and out-of-band.
SQLMap lets you run any command and get its standard output, download and upload any file, look for specific database names, and more. It will let you join the database right away.
Website: SQLMap
#8) NetStumbler

NetStumbler is a tool for wireless networking. It works with Windows OS. The 802.11b, 802.11a, and 802.11g WLAN are used to find wireless LANs. It also has a smaller version called MiniStumbler that works on Windows CE OS mobile computers. It has support built right in for a GPS unit.
You can use NetStumbler to check your network settings, find spots in a WLAN that don’t have good service, find sources of wireless interference, find unauthorized access points, and more.
Website: NetStumbler
#9) Ettercap

Price: Free.
Cross-platform works with Ettercap. You can make your plugins using Ettercap’s API. Even if you use a proxy, it can sniff HTTP SSL-encrypted data.
Features:
- Live links are being sniffed.
- Filtering the content.
- Breaking down many rules in both active and passive ways.
- Analysis of the network and hosts.
- Best for making your plugins.
Website: Ettercap
#10) Maltego

Price: Maltego CE, the community version, is free to use. Maltego Classic costs $999. Maltego XL costs $1999. These two things are for your desk. Products for servers like CTAS, ITDS, and Comms start at $400,000, and that price includes training.
Maltego can be used for link analysis and data mining. It’s compatible with OSes like Linux, Windows, and Mac OS X.
It gives you a library of changes that you can use to find data from open sources and see it in the form of graphs. It gathers information and mines data in real-time.
Features:
- Shows info on graph patterns based on nodes.
- Maltego XL can handle big graphs.
- It will show you a graph that shows you where the network is weak and where things aren’t working right.
- The best way to work is with massive graphs.
Website: Maltego
Conclusion
As this page explains, Nmap is used to keep computers safe and handle networks. It works well to search the network. Metasploit is also used for security and is suitable for making tools that hide from forensics and hackers.
You can get Aircrack-Ng for free, and it works on multiple platforms and can sniff and insert packets. As a packet analyzer, Wireshark can look at data packets and do an excellent job. Online reviews say that Nmap is better than Angry IP Scanner because Angry IP Scanner comes with extra programs that you don’t want.
John the Ripper can break passwords quickly. Nikto is an excellent open-source tool for testing for security holes. The data is shown in a graph by Maltego, which also tells you about weak spots and other problems.